λ Blog.
Earnest posting amidst a sea of irony and generative content.
We've done Pip-Boy discovery and relay, creating new libraries in the process. Now it's time to put them to good use by building a multiplayer map. To get us there, I will show you how to use Observables to handle streams of player data and render them onto a map.

More Stories
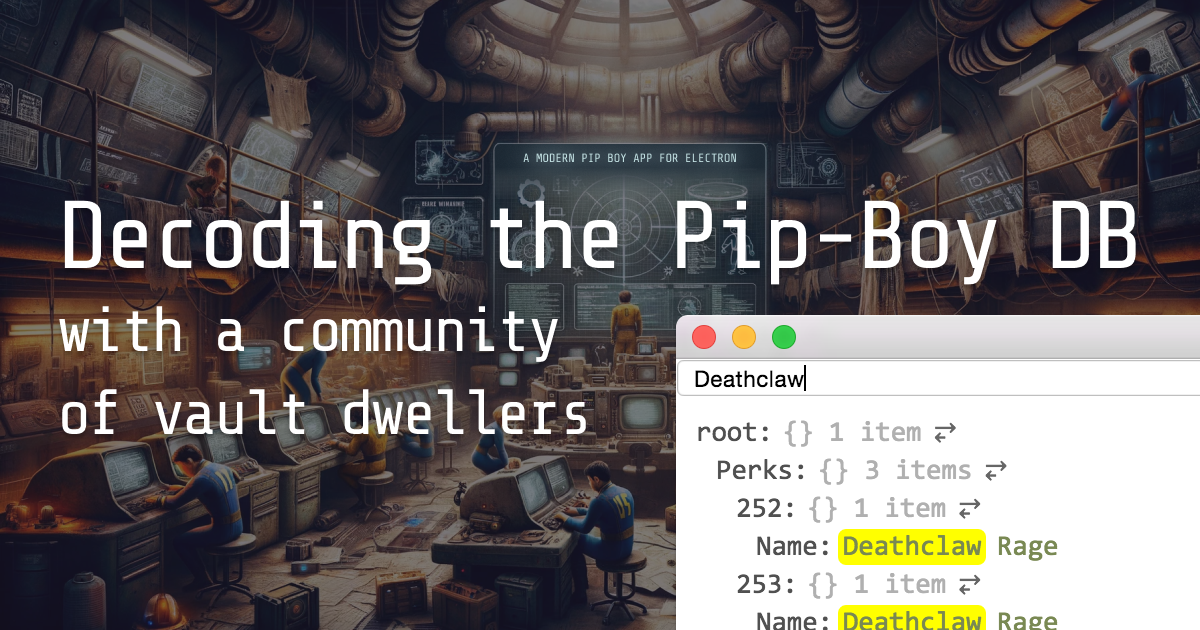
Decoding Fallout 4's Pip-Boy database with a community of vault dwellers
Following the siphoning of traffic from the Pip-Boy mobile app and Fallout 4 game, a community of hackers came together to decode the Pip-Boy data and database.
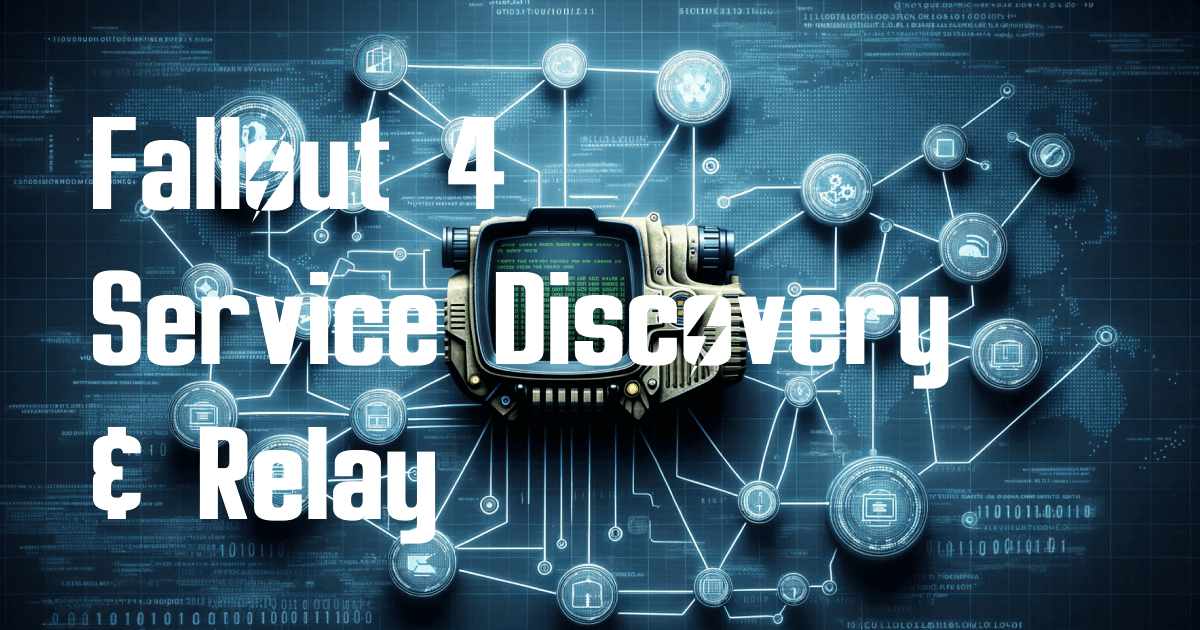
Fallout 4 Service Discovery and Relay
Take apart the pip boy app, discover running Fallout 4 games, and relay traffic with a bit of Node.js, TCP, and UDP.
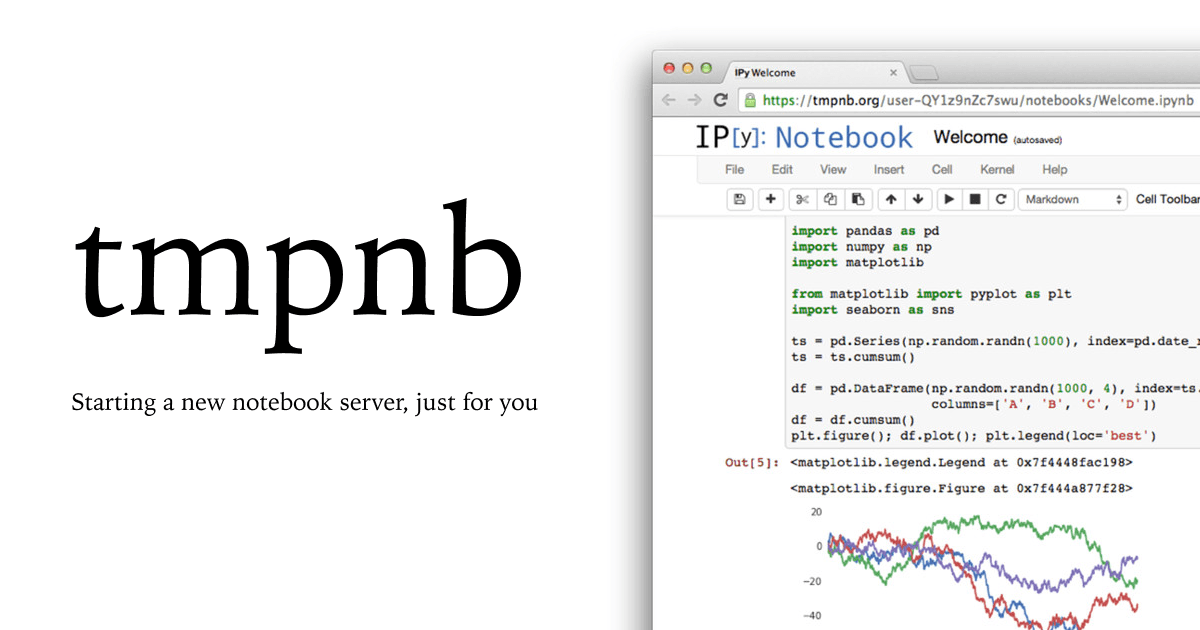
Ops Lessons on Instant Temporary IPython Notebooks
Running hundreds of thousands of notebook servers on demand for Nature readers taught us many lessons. It fundamentally changed how we develop and deploy Jupyter.
Instant Temporary IPython Notebooks
How I went from prototyping with Docker and an HTTP Proxy to launching ephemeral notebook services on demand with Project Jupyter.